Arguably one of the most important concepts when it comes to security is Defense in Depth. This principle is essential when designing and implementing an effective security plan. In the simplest of terms, Defense in Depth refers to the layering of multiple security controls within your organization. The idea behind layering controls is so if one fails, another exists beyond it to prevent a full system compromise. While your mind may immediately drift to physical security controls such as fences, guards, and building access; this concept applies to both the cyber and physical realms.
In order to better understand Defense in Depth and how it is effective, we will look at diagram I drew up. First, we will focus on physical security since it’s the easiest to envision. By the way… I am using Paint, so I apologize for the crap picture. If any of you know where I can create diagrams FOR free, please drop me a line in the comments! I will be forever grateful.
Defense in Depth in the Physical Realm
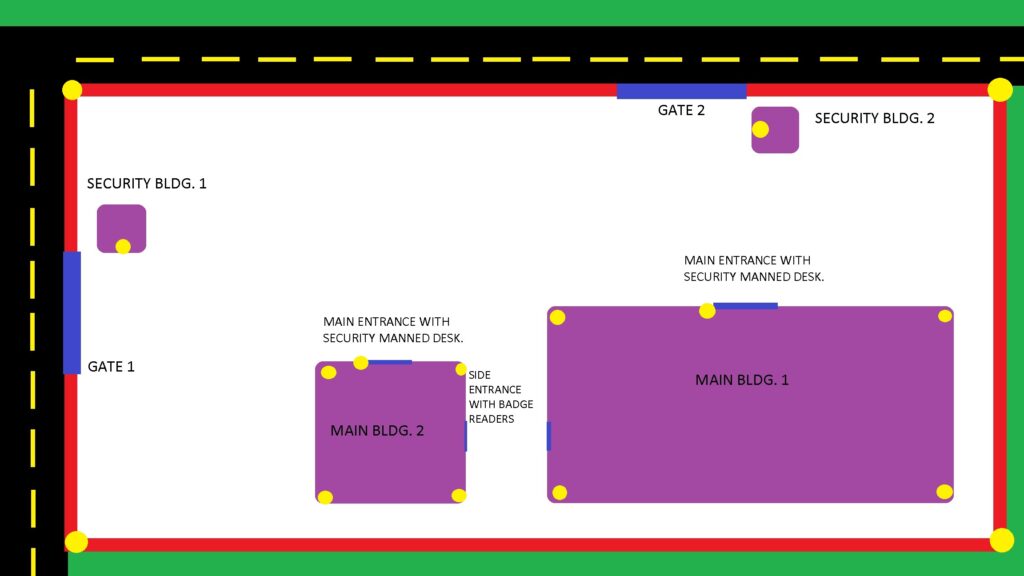
So, let’s start by going over what each of these colors and shapes represent. First off, the red line surrounding the exterior of the property is your perimeter fence or wall, whichever you prefer to imagine. All of the purple squares are buildings of sorts while the blue indicates an entryway. Finally, the yellow dots peppered around represent possible locations of security cameras.
Having a wall with a limited amount of entry points forces all employees and visitors into a chokepoint in which you can dedicate your security staff. From here you are able to vet traffic coming in and out of your facility. Yet people are all prone to mistake. This applies to both the staff and visitors. People who unauthorized intentionally or by mistake will slip by these initial chokepoints eventually. This is why we have additional layers of security in the form of manned stations at each building entry. Here visitors can also get visitor credentials and directed to their proper place.
Also take note that I have marked the side entrances as having badge readers. This is another important feature of a secure physical system as you can track individuals’ comings and goings. It also automates the security at the side entrances so you can free up your personnel for other uses. This is also the idea for the placing of cameras all over the compound. They allow for a single camera operator to monitor multiple points simultaneously. They also serve an additional use creating the appearance of a “hard target”. This is directly opposed to a “soft target”. I hope to write a post in the future going more in depth of this topic but for now know soft target = easy target; hard target = prepared target. Appearing prepared can act as deterrence in many situations and make malicious actors think twice.
The concept that I am trying to really drive home is that this system is not dependent on ONE SINGLE CONTROL but a group of them dispersed. It is essential to not have a single point of failure system. It takes more effort to exploit a decentralized security system over a centrally controlled one.
Defense in Depth in the Cyber Realm
As we move from the physical world to the digital one, I want to point out that the concepts here do not change. We do not want a single point of failure when it comes to our security controls. Therefore, when planning our network defense, we must have multiple overlapping security controls. These controls can be both technical (firewalls, VPN, etc.) or administrative (password change frequency policy, access-control policies, etc.). Obviously, most companies and government organizations utilize both technical and administrative controls to mitigate cyber-attacks.
Another important concept we touched upon earlier is the difference between a soft-target and a hard-target. This also applies here. Just think about it this way, if a hacker scans your network and sees a bunch of unnecessary ports running vulnerable services, he says “easy day, I can pwn this machine in 5 mins!”. Now your network is f’d. Otherwise, if your network is scanned and he can’t even scan or all your ports are locked down, it may not be worth his time and effort or beyond his skill level. So, in both physical and cyber security, your outward facing security appearance plays a critical role.
To really demonstrate how defense in depth works in the cyber realm, we are going to use an old Visio drawing from one of my school projects. I am very cheap so there is no way I will be using Visio if I have to pay for it. This is just a disclaimer in case you are wondering why I used paint for the first diagram and have a nice fancy Visio Diagram below.
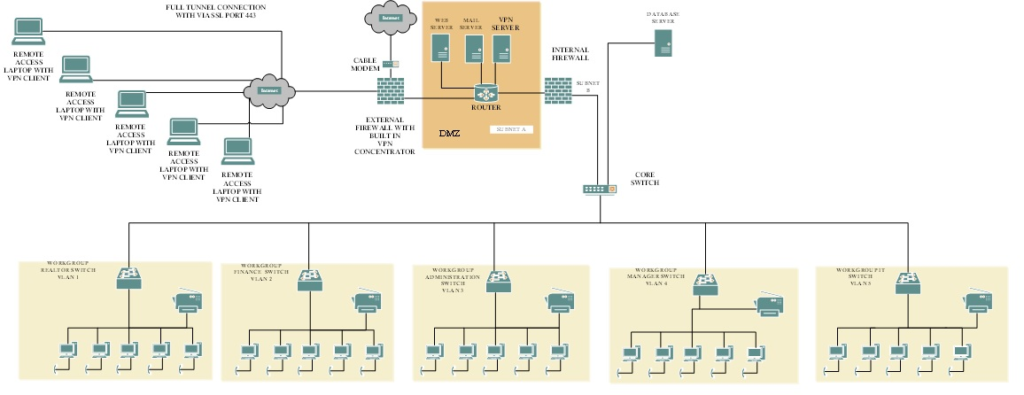
I’d first like to apologize for the blurry nature of the photo above. When I re-sized it for the site, we lost a little bit. Hopefully, you can read this enough to get an idea what we are talking about. Just as a general overview, the task when creating my project was to generate a network diagram for a medium-sized business utilizing security best practices. Each department is on their own VLAN (virtual local area network) which then connects to the network core switch. Off of this core switch we have our database server and our internal firewall at the boundary. These items form our internal network. We then have our DMZ (demilitarized zone) which features all of our external facing network devices, another firewall, and our remote users.
I am sure some of you will critique and hate on my design, but I don’t care… I don’t get paid to design networks. I’m here to talk about Defense in Depth. In doing such we will start with the network flow externally then work inwards pointing out security controls and how they overlap with one another.
Let’s start out with a local user in our Finance Department. The first layer of defense is actually the physical security controls of the building. Once inside, the employee must have proper credentials to log into the machine to prevent unauthorized users from accessing the network. Yet if this control is somehow bypassed (or insider threat) each workstation is logically isolated to a small LAN, not to the greater network. If one somehow got beyond this control, we could use subnetting on the core switch to avoid any further compromise. You can choose to add more layers of security beyond this but once you add too many controls you may notice a slow-down of your network or increased operating costs. Like everything in life, it’s all about balance.
As in physical security realm, each layer presents another opportunity to prevent unauthorized use or access. Being dependent on just one control creates a single point of failure and increases your odds of total system compromise. When utilizing a layered security plan or Defense in Depth you distribute controls over multiple areas providing more places for the security violation to be stopped.

